Where is the risk?
It’s everywhere.
Being single is a risk of loneliness and depression.
Being in a live-in relationship is a risk of an uncertain future.
Being married is a risk of missing bachelorhood.
Whether it’s relationship or data, you can never eliminate the risk. All you can do is reduce it to the accepted level.
Risk management is CISSP’s core concept. You already apply risk management in so many ways in day-to-day life. You are not just aware of it.
I have diverse metaphor options for deadly animals in Australia to represent the risk. My favourite is Redback Spider.
Let’s Hike
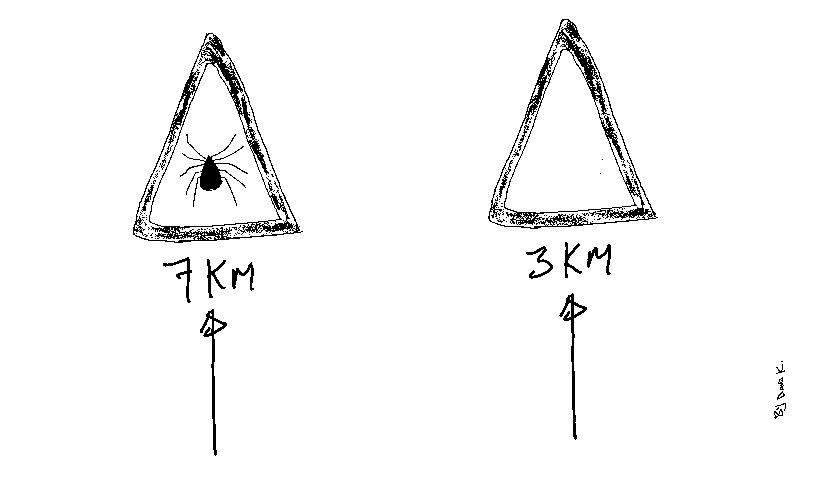
You are on your favourite hiking track with your girlfriend. The circuit is 7km with medium-to-high difficulty levels.
Risk Mitigation
Risk reduction is a choice you want to go ahead despite the danger. However, you will take precautions to keep Redback Spider away, such as carrying an emergency first-aid kit and ice pack and wearing full pants, gloves and shoes.
Countermeasures against the Redback Spider Addressing safeguards is about implementing security controls. It reduces the risk to a reasonable level. However, the risk is still there (residual risk). What if Redback bites on your neck or ear?
Only mitigate the risk when the reduction cost is lower than the benefits gained.
The cost of security countermeasures must make sense from the business perspective.
Risk Avoidance
Risk avoidance is a wise choice. Why risk life if there is the danger?
Indeed, the ocean panorama at the end of 7km would give you a magnificent view, but is it worth it?
Can you take an alternate 3km trail? It won’t challenge your fitness and give the best scenery, but no danger sign board exists.
From a business context, the solution may cost 30% less than other vendors, but is it worth risking the organization’s reputation and the high possibility of sensitive data leakage?
No.
Avoid the risk when the risk mitigation or acceptance cost exceeds the benefits gained. The best way to deal with such risk is to avoid it.
Consider alternatives to achieve the same or similar or desired outcomes.
Risk Assignment
You are scared of the spider, but your girlfriend researches the Redback spider. Dealing with such dangerous creatures is her day-to-day work. You decide to sit in the car if you don’t mind. Let her do the hiking and take that panoramic ocean photo for you.
You have just transferred the risk!
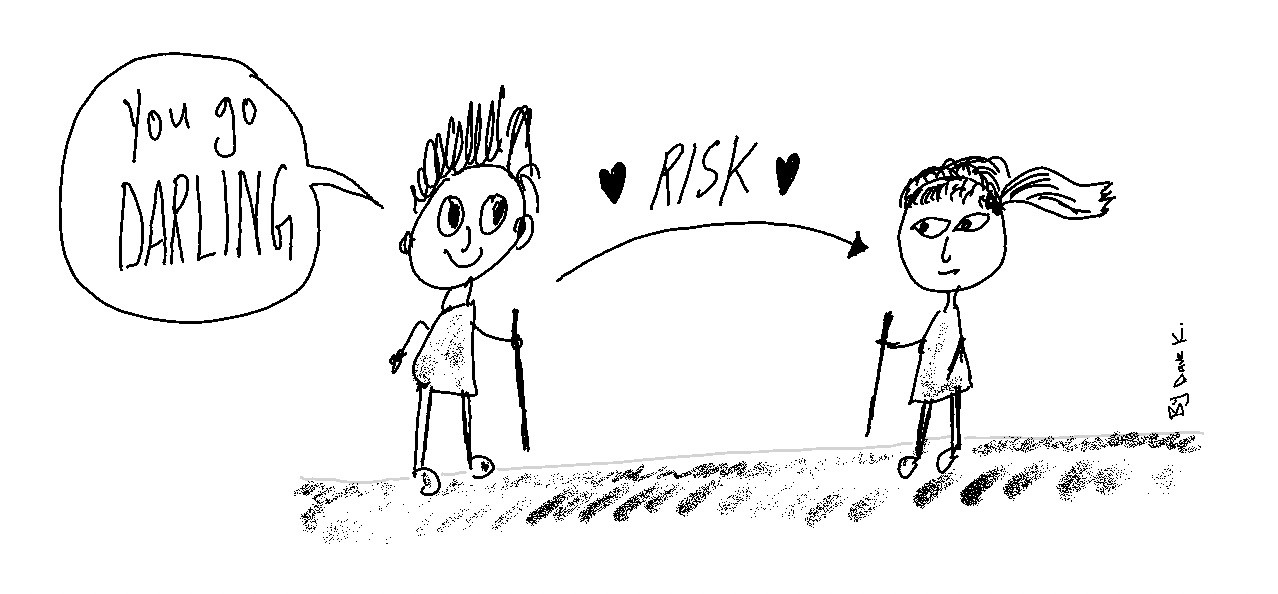
Risk transfer is a clever choice.
We do assign the risk when we purchase a car or health insurance. None of us will have a road accident or heart attack every day. But we still buy the insurance for peace of mind.
It makes sense to transfer the risk when the likelihood is low, and the risk is high.
Most of the on-premise applications are migrating to cloud SaaS (Software-as-a-service). At the core, there is a lot of risk transfer from the business end.
Risk Acceptance
You don’t care about Redback Spider because you are unafraid of the spider. You are aware of the consequences. You are ready to fight.

It’s about your risk tolerance. There are circumstances when businesses are aware of the risk, but they still give the green signal to go ahead. Risk appetite certainly requires thorough cost/ benefit analysis before accepting the risk.
Accept when the risk and exposure are low.
Risk Deterrence
You see the below warning sign at the entrance of the trail. It’s a passive risk response. It’s about letting people know the possibility of dangerous spiders before hiking.

Implementing security policies such as patch management, CCTV cameras, and security guards is an example of risk deterrence.
Risk Rejection
You ignore the danger signs and decide to hike without the required protections. Risk rejection is a foolish choice where you hope nothing will happen. However, there is always a price for such ignorance.

You will get rid of the risk. However, you can respond to risk based on budget constraints, risk appetite and other factors.
During the last summer holiday, my son said, “I don’t want to go on that giant roller coaster. Let’s go to the smaller one.”
What kind of risk response did he choose?
Let me know your thoughts in the comments. Please share your analogies on understanding risk responses.



Your son recognized that the giant roller coaster might be too risky, scary, or uncomfortable so he chose to avoid that risk entirely by picking a smaller, safer alternative.
So its “risk avoidance”
“Avoid the risk when the risk mitigation or acceptance cost exceeds the benefits gained. The best way to deal with such risk is to avoid it.”
He didn’t try to fight the fear (risk acceptance), didn’t use safety gear to try and manage it (risk mitigation), didn’t transfer the risk to someone else (risk Assignment), nor did he ignore it (risk rejection). He simply chose a different path which is the essence of risk avoidance.
Spot on, Sathish
You have demonstrated solid understanding of the concept by writing a mini post in the comment 😊